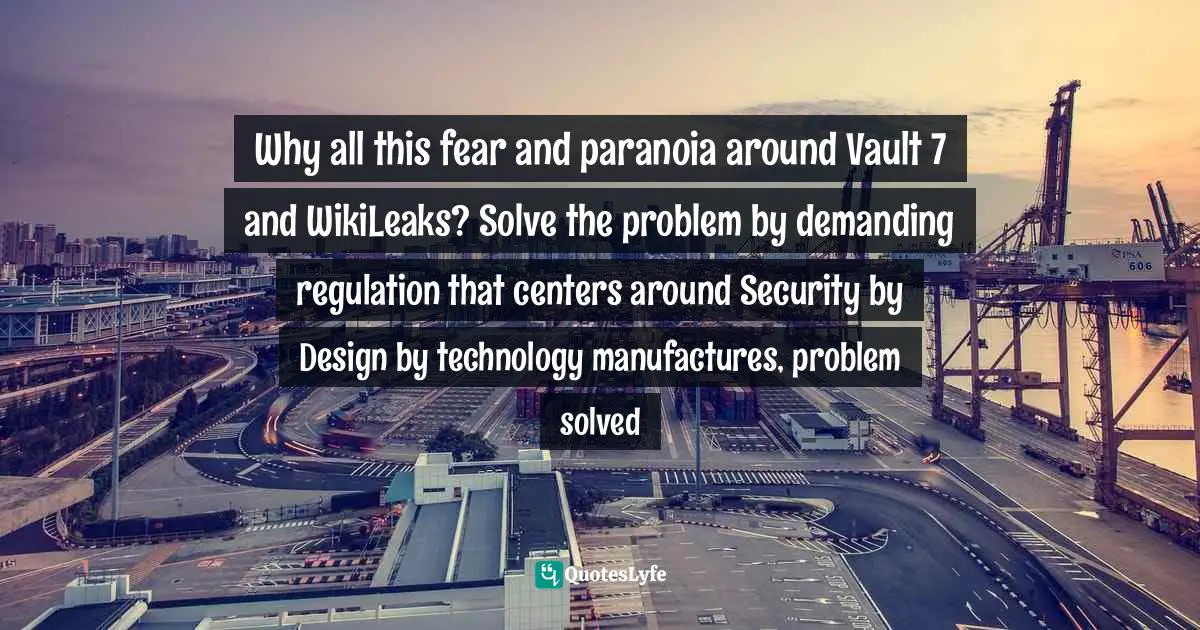
Every conceivable layer of the election process is completely riddled with vulnerabilities, so yes, hacking elections is easy!
 James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
Check all other quotes by James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
Want to display this quote image on your website or blog? Simply copy and paste the below code on your website/blog.
Embed:Format of this image is jpg. The width and height of image are 1200 and 630, repectively. This image is available for free to download.
Citation
Use the citation below to add this quote to your bibliography:
MLA Style Citation
"James Scott, Senior Fellow, Institute for Critical Infrastructure Technology Quotes." Quoteslyfe.com, 2025. Fri. 31 Jan. 2025. <https://www.quoteslyfe.com/quote/Every-conceivable-layer-of-the-election-process-254793>.
Check out
Other quotes of James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
Other quotes you may like
Quote Description
This page presents the quote "Every conceivable layer of the election process is completely riddled with vulnerabilities, so yes, hacking elections is easy!". Author of this quote is James Scott, Senior Fellow, Institute for Critical Infrastructure Technology. This quote is about malware, cybersecurity, election-2016, elections, phishing, election, hacking, voting, security,.